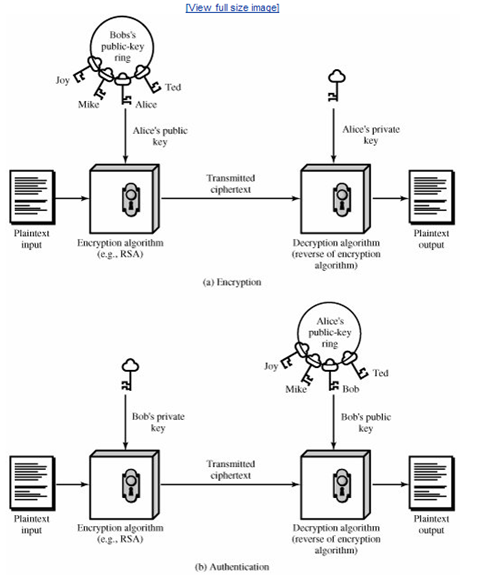
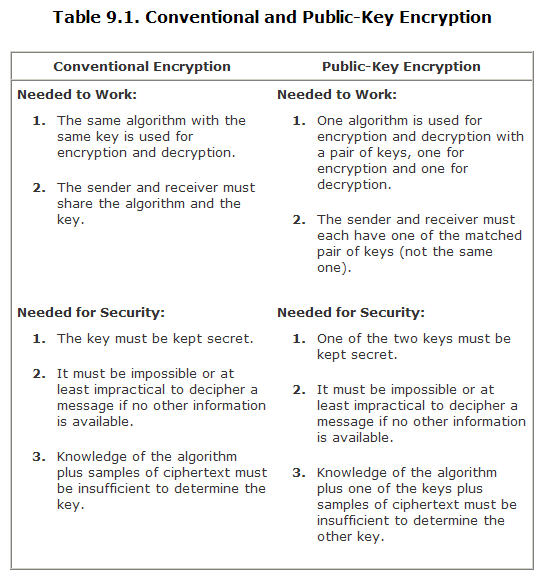
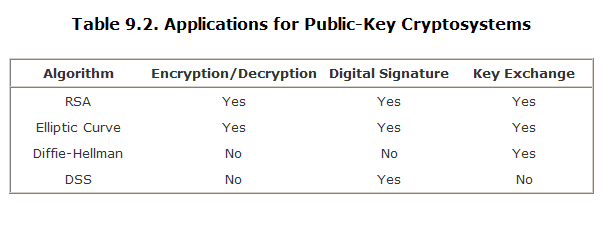
-
Use of public key-scheme in key distribution:
-
The distribution of public keys.
- Public announcement.
- Publicly available directory.
- Public-key authority.
- Public-key certificates.
- The use of public-key encryption to distribute secret keys.
-
- Public announcement of keys has one weakness in that anyone can forge key and then the forger pretend as being authenticated participant.

-
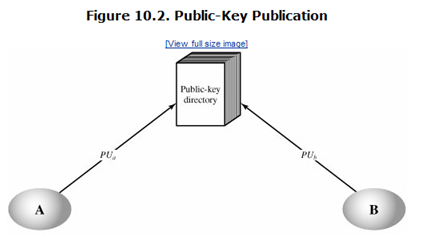
Elements of Publicly Available Directory:
- The authority maintains a directory with a {name, public key} entry for each participant.
- Each participant registers a public key with the directory authority.
- A participant may replace the existing key with a new one at any time.
-
Participants could also access the directory electronically.
- So, secure, authenticated communication from the authority to the participant is mandatory.
- The weakness of this scheme is that if an adversary succeeds in obtaining or computing the private key of the directory authority, the adversary could authoritatively pass out counterfeit public keys.
- 292-Steps for successful message exchange in public-key authority.
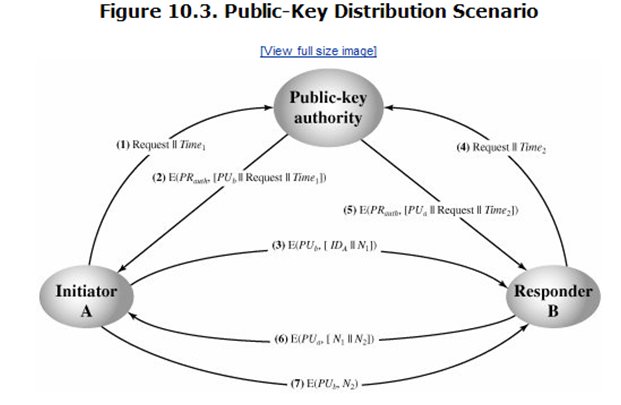
- A technique known as caching. Periodically, a user should request fresh copies of the public keys of its correspondents to ensure currency.
-
Requirements for Public-Key Certificate:
- Any participant can read a certificate to determine the name and public key of the certificate’s owner.
- Any participant can verify that the certificate originated from the certificate authority and is not counterfeit.
- Only the certificate authority can create and update certificates.
- Any participant can verify the currency of the certificate.
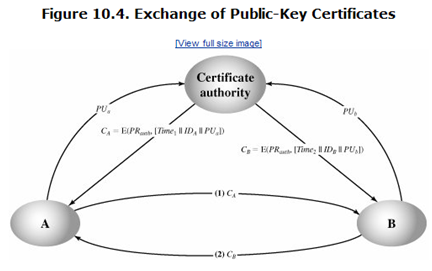
- The timestamp T validates the currency of the certificate (i.e. that the current certificate is what B’s has).
-
Simple Secret Key Distribution Communication Steps:
- A generates a public/private key pair {PUa, PRa} and transmits a message to B consisting of PUa and an identifier of A, IDA.
- B generates a secret key, Ks, and transmits it to A, encrypted with A’s public key.
- A computes D(PRa, E(PUa, Ks)) to recover the secret key. Because only A can decrypt the message, only A and B will know the identity of Ks.
- A discards PUa and PRa and B discards PUa.
- Man-in-the-middle attack is a form of active attack in which the attacker intercepts and selectively modifies communicated data in order to masquerade as one or more of the entities involved in a communication.
- 296-Read how an adversary can compromise the communication between two entities without being detected.
-
Steps for Secret Key Distribution with Confidentiality and Authentication:
- A uses B’s public key to encrypt a message to B containing an identifier of A (IDA) and a nonce (N1), which is used to identify this transaction uniquely.
- B sends a message to A encrypted with PUa and containing A’s nonce (N1) as well as a new nonce generated by B (N2) Because only B could have decrypted message (1), the presence of N1 in message (2) assures A that the correspondent is B.
- A returns N2 encrypted using B’s public key, to assure B that its correspondent is A.
- A selects a secret key Ks and sends M = E(PUb, E(PRa, Ks)) to B. Encryption of this message with B’s public key ensures that only B can read it; encryption with A’s private key ensures that only A could have sent it.
- B computes D(PUa, D(PRb, M)) to recover the secret key.

- A hybrid scheme retains the use of a key distribution center (KDC) that shares a secret master key with each user and distributes secret session keys encrypted with the master key. A public key scheme is used to distribute the master keys.
Diffie-Hellman Key Exchange
- The purpose of the algorithm is to enable two users to securely exchange a key that can then be used for subsequent encryption of messages. The algorithm itself is limited to the exchange of secret values.

- The security of the Diffie-Hellman key exchange lies in the fact that, while it is relatively easy to calculate exponentials modulo a prime, it is very difficult to calculate discrete logarithms. For large primes, the latter task is considered infeasible.
- If the exchange of YA and YB was not secure a man-in-the-middle attack may occurs.
Elliptic Curve Arithmetic
- The principal attraction of ECC, compared to RSA, is that it appears to offer equal security for a far smaller key size, thereby reducing processing overhead.
- Elliptic curves are not ellipses. They are so named because they are described by cubic equations.
y2 + axy + by = x3 + cx2 + dx + e